Posts Tagged 'Security'
-
April 10, 2024
Cryptomathic and Marvell: Enhancing Crypto Agility for the Cloud
By Bill Hagerstrand, Director of Security Solutions at Marvell
Grab a cup of coffee. In this blog I describe how IT professionals can utilize Marvell® LiquidSecurity® Hardware Security Modules (HSMs) with Cryptomathic’s Crypto Service Gateway.
Cryptomathic has 35+ years of experience providing global secure solutions to a variety of industries, including banking, government, technology manufacturing, cloud, and mobile. The company’s Crypto Service Gateway software is a first-of-its-kind central cryptographic platform that provides centralized and crypto-agile management of third party HSM hardware, enhancing the behavior of HSMs while improving the time-to-market of business applications.
An HSM is a physically secure computing device that safeguards and manages digital keys, performs encryption/decryption functions, and provides strong authentication mechanisms. They typically come in two form factors: a PCIe card or a 1U network attached server. They are NIST (National Institute of Standards and Technology) FIPS 140-3, level-3 certified and most provide tamper evidence (visible signs of tampering), tamper resistance (the HSM becomes inoperable upon tampering) or tamper responsive (deletion of keys upon tamper detection). All provide logging and alerting features, strong authentication, and key management features, and support common APIs like PKCS#11. Applications that require cryptographic services will make API calls for keys used to encrypt data in motion or at rest.
-
April 10, 2024
HashiCorp and Marvell: Teaming Up for Multi-Cloud Security Management
By Bill Hagerstrand, Director of Security Solutions at Marvell
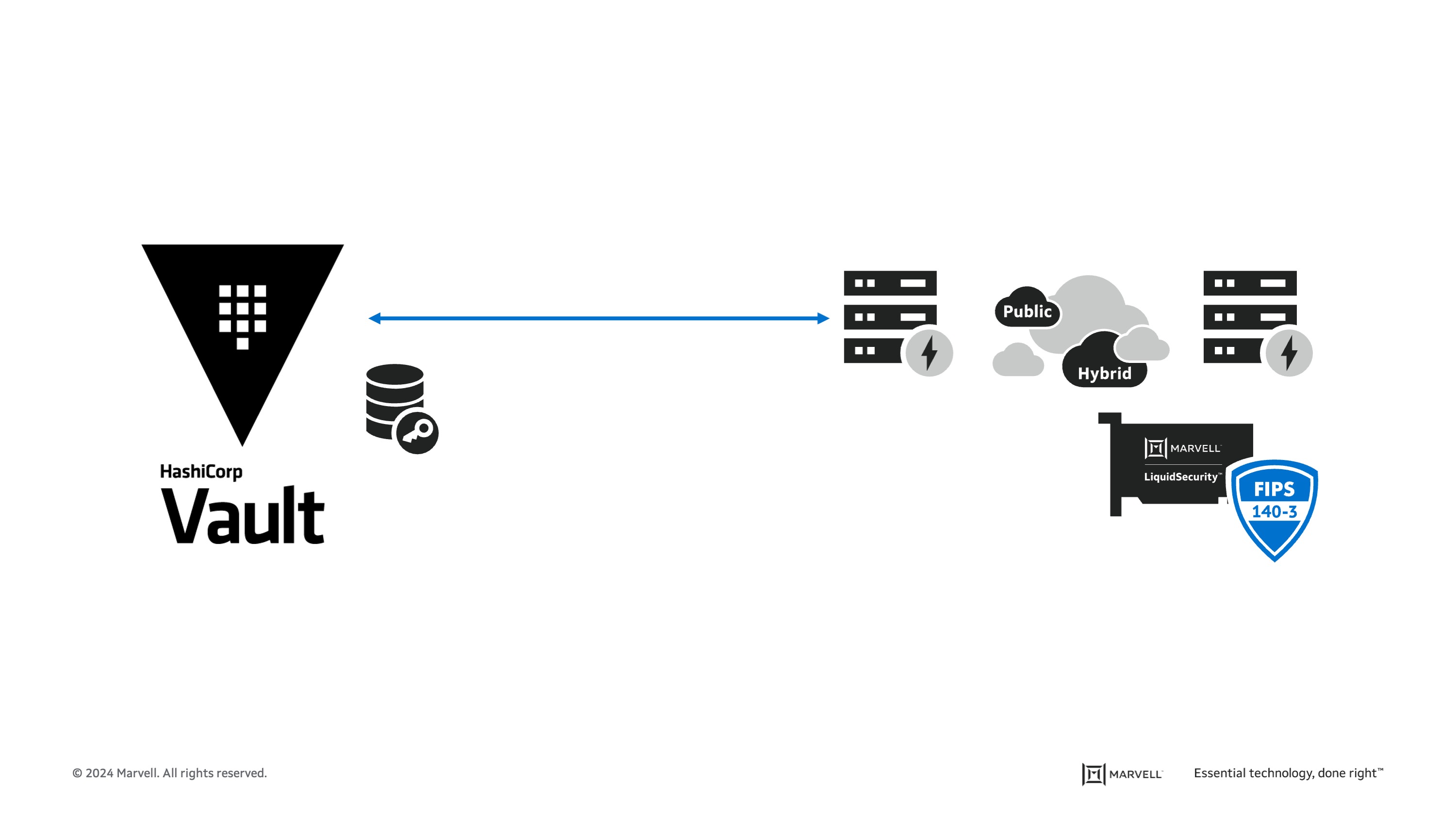
In this blog I describe how cybersecurity professionals can utilize Marvell® LiquidSecurity® HSMs with self-managed HashiCorp Vault Enterprise software, deployed on-prem and in the cloud.
HashiCorp provides infrastructure automation software for multi-cloud environments, enabling enterprises to unlock a common cloud operating model to provision, secure, connect, and run any application on any infrastructure. HashiCorp Vault provides the foundation for modern multi-cloud security. It was purpose-built in the cloud era to authenticate and access different clouds, systems, and endpoints, and centrally store, access, and deploy secrets, i.e. encryption keys, passwords, API tokens, tokens used in applications, services, privileged accounts, or other sensitive portions of the IT ecosystem. It also provides a simple workflow to encrypt data in flight and at rest. Global organizations use Vault to solve security challenges as they adopt cloud and DevOps-friendly solutions.
-
April 09, 2024
The Big, Hidden Problem with Encryption and How to Solve It
By Bill Hagerstrand, Director of Security Solutions at Marvell
Data encryption, invented nearly 50 years ago1, remains one of our most valuable tools for securing data.
It is also woefully under-utilized.
The most recent Entrust-Ponemon survey shows that 62% of enterprises have an encryption strategy in place, which is another way of saying 38% don’t2. (In 2021, it was 49%3.). 入力された製品またはテクノロジーの米国 Department of Health and Human Services imposes millions in fines per year on healthcare organizations for improper snooping of medical records by employees, or health records accidentally released when a doctor’s laptop gets stolen. And, although 60% got hit with ransomware attacks this year, only 24% were able to thwart an attack by encrypting it before the hackers could.
So, what’s the hang up?
Inertia. For all of its effectiveness, encryption has historically been difficult and/or inconvenient to use (in part, of course, for the need to keep access tight.) It requires cooperation between both the sender and receiver and adds additional processing power and time. How many of your personal emails or messages do you encrypt? One of the most widespread and successful uses of encryption in the consumer world—encrypting the data for financial transactions on phones—has succeeded in part because it takes the encryption process out of the hands of consumers and makes it a back-end function. Back-end encryption functions, meanwhile, are also typically performed on a hardware security module (HSM), a 1U to 2U appliance that companies historically kept on premise and maintained on their own.
-
January 14, 2021
What’s Next in System Integration and Packaging? New Approaches to Networking and Cloud Data Center Chip Design
By Wolfgang Sauter, Customer Solutions Architect - Packaging, Marvel
The continued evolution of 5G wireless infrastructure and high-performance networking is driving the semiconductor industry to unprecedented technological innovations, signaling the end of traditional scaling on Single-Chip Module (SCM) packaging. With the move to 5nm process technology and beyond, 50T Switches, 112G SerDes and other silicon design thresholds, it seems that we may have finally met the end of the road for Moore’s Law.1 The remarkable and stringent requirements coming down the pipe for next-generation wireless, compute and networking products have all created the need for more innovative approaches. So what comes next to keep up with these challenges? Novel partitioning concepts and integration at the package level are becoming game-changing strategies to address the many challenges facing these application spaces.
During the past two years, leaders in the industry have started to embrace these new approaches to modular design, partitioning and package integration. In this paper, we will look at what is driving the main application spaces and how packaging plays into next-generation system architectures, especially as it relates to networking and cloud data center chip design.
-
October 07, 2020
車載アプリケーション向けイーサネット高度機能
マーベル、オートモーティブ・ビジネス・ユニット、マーケティング担当バイス・プレジデント、アミール・バー・ニヴ氏著
イーサネット標準は、実際のネットワークのニーズを解決し、 セキュリティの脅威を解決するために、長年にわたって開発されてきた 機能とソリューションの長いリストで構成されている。 現在、イーサネット車載ネットワーク(IVN)の開発者は、 車両のネットワークに欲しい機能を選択することで、 機能性とコストのバランスを容易にとることができる。
イーサネット技術のルーツは1973年に始まった。その時、 ゼロックス研究センターの研究員(後に3COMを設立)のボブ メトカーフが、 短距離の銅線ケーブルでコンピュータを接続する方法を説明した「Alto Ethernet」 というタイトルのメモを書いた。 1980年代に企業や法人のPCベースのローカルエリアネットワーク(LAN)の爆発的な普及に伴い クライアント/サーバー型LANアーキテクチャの成長 が続き、イーサネットが接続技術の選択肢 の1つになり始めている。 しかし、イーサネットの進歩により、 これまでで最も成功したネットワーキング テクノロジとなったのは、 IEEE 802.3グループの下でイーサネットの標準化の取り組み が始まったときだった。
最新の記事
- HashiCorp and Marvell: Teaming Up for Multi-Cloud Security Management
- Cryptomathic and Marvell: Enhancing Crypto Agility for the Cloud
- The Big, Hidden Problem with Encryption and How to Solve It
- Self-Destructing Encryption Keys and Static and Dynamic Entropy in One Chip
- Dual Use IP: Shortening Government Development Cycles from Two Years to Six Months

